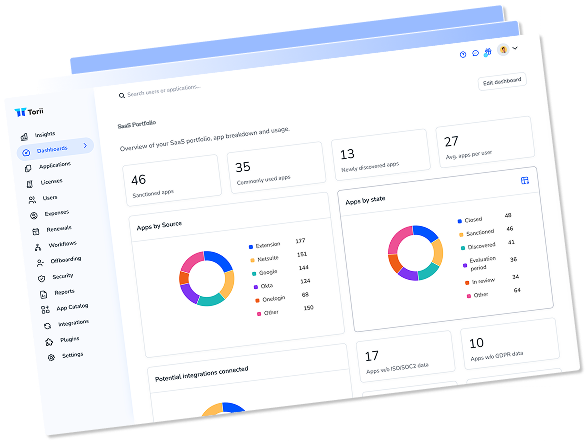
Why SaaS Management Is Critical for Cybersecurity
Most CISOs agree SaaS speeds up work, yet its blind spots pile up fast. A free trial started during lunch or a card-based subscription buried in an expense report can hit production before security even hears about it. Each unvetted URL adds risk, cost, and compliance headaches.
A SaaS management platform puts IT and security on the same page at last. It surfaces sign-ups, stale credentials, and duplicate licenses, and then lets teams fix issues in minutes instead of weeks. Domain mapping, automated revocation, and role templates replace spreadsheet guessing with continuous proof of control.
With that visibility, teams can treat SaaS like any other piece of managed infrastructure. They discover every app, cut off orphaned tokens, trim the stack, and enforce least privilege from one console. SaaS turns from liability to defensible asset.
Table of Contents
- Shedding Light on Shadow IT Risks
- Sealing Access Gaps When People Leave
- Reining In Runaway SaaS Sprawl
- Standardizing Permissions for Least-Privilege Safety
- Conclusion
- Audit your company's SaaS usage today
Shedding Light on Shadow IT Risks
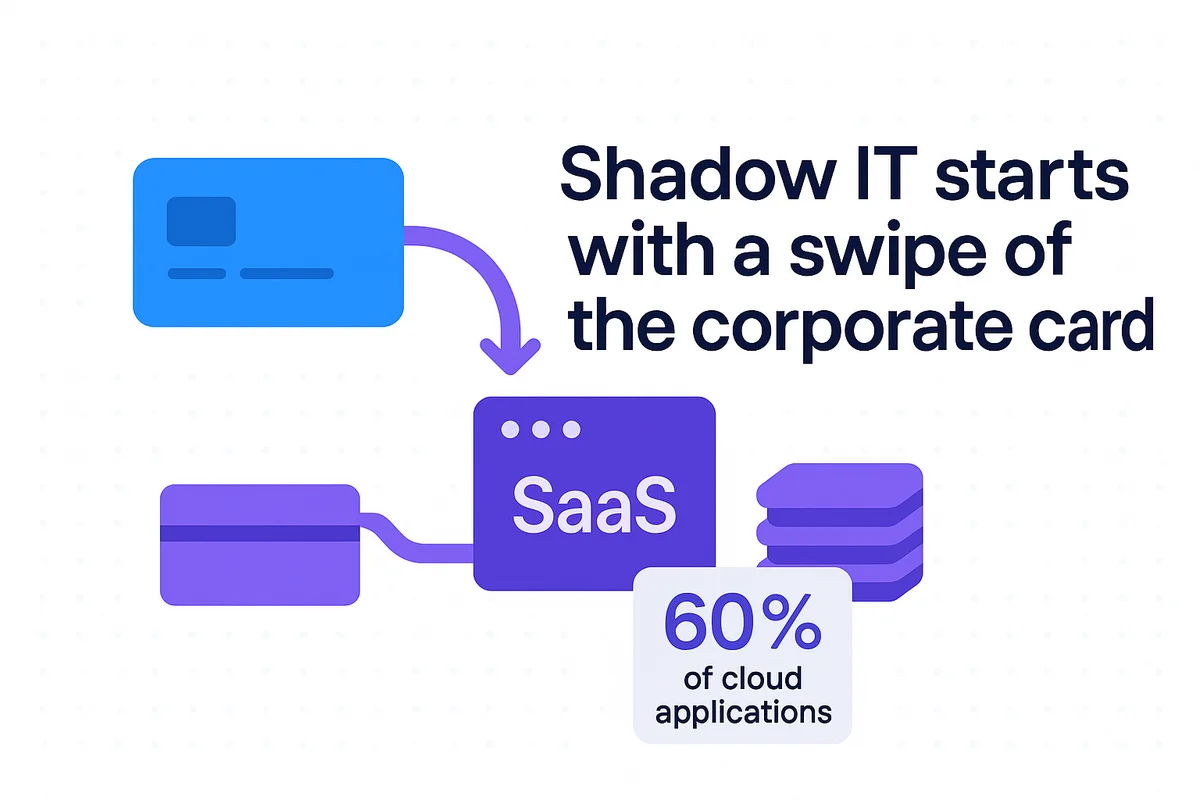
Shadow IT often begins with a quick swipe of the corporate credit card.
Unapproved SaaS sign-ups pile up quickly across marketing and design teams. Gartner estimates that 60 percent of cloud applications in the average enterprise are now sourced outside IT, which means sensitive files, PII, and even code repositories move into services no one has vetted. When CISOs cannot see the traffic, they cannot enforce DLP, test vendor controls, or prove compliance during an audit, so a small freemium trial can spiral into a data-exfiltration headline.
SaaS management platforms cut through that fog by watching activity inside the tools instead of waiting for a help-desk ticket. Browser extensions record every unknown domain a user logs into, API connectors pull exact user and permission lists from major SaaS vendors, and network log analysis spots tools that bypass SSO altogether. Because those data streams feed the same engine, security gains a living map of the SaaS estate rather than a quarterly spreadsheet snapshot.
Detection is only half the job; the other half is real-time response that beats an attacker’s dwell time. Modern platforms attach a risk score the moment a new domain appears, then push that context into Slack, Teams, or the SIEM so analysts can act while the ink is still drying on the signup form.
- Quarantine high-risk apps until a formal review finishes
- Force SSO on medium-risk tools before any data flows
- Auto-block copycat domains that mimic company branding
The cycle produces a feedback loop: every new discovery hardens the next one, and the security team trades guesswork for evidence. Continuous visibility, instant classification, and one-click containment turn shadow IT from an unmanageable headache into a measurable, coachable process.
Sealing Access Gaps When People Leave
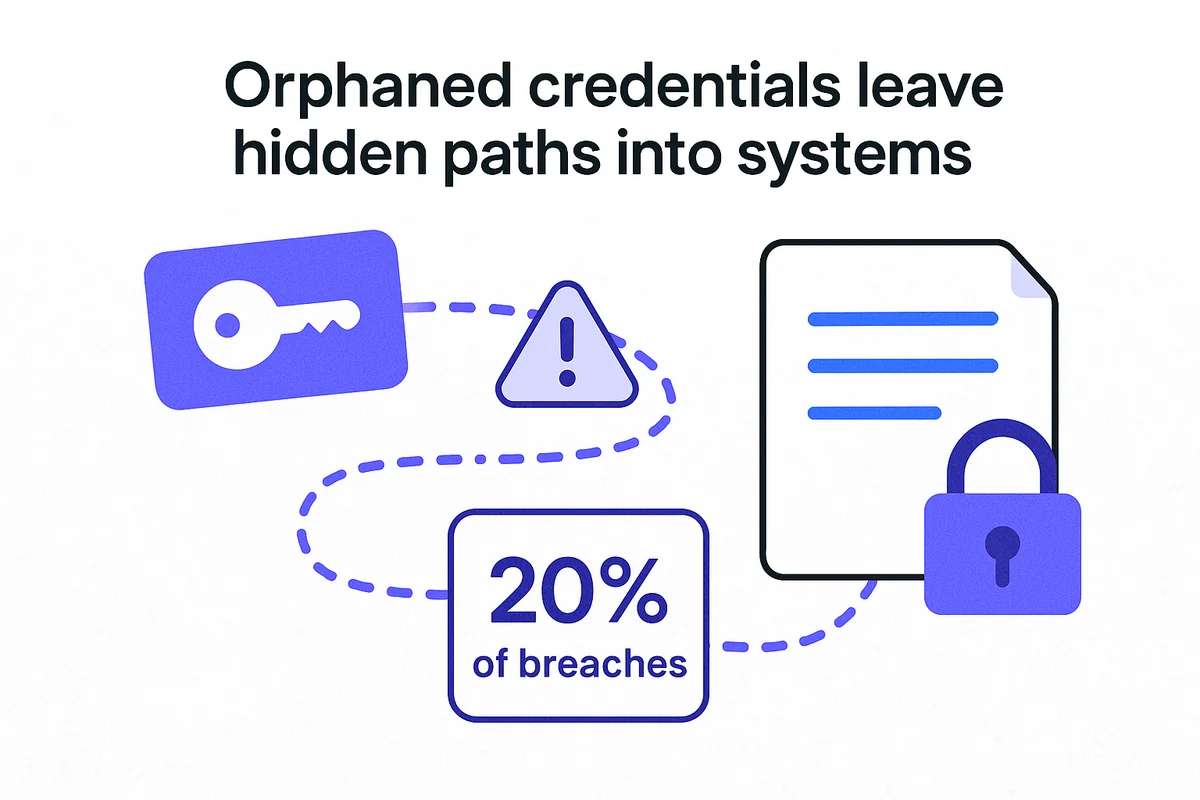
Offboarding gaps leave hidden paths into systems long after employees depart. Verizon’s latest DBIR attributes nearly 20 percent of breaches to insiders, with orphaned credentials topping the list. When Heroku and Travis CI were hacked in 2022, GitHub removed thousands of forgotten OAuth tokens issued to former users, underscoring how neglected access invites trouble.
Revoking access seems simple until you are staring at 40 different dashboards, each with its own toggle. HR marks the person as terminated, yet IAM, CRM, and half a dozen project boards never receive the memo. A single misclick keeps a power user’s API key alive, and an ex-contractor can still pull customer data from a laptop in a café.
SaaS management platforms turn that scramble into a repeatable flow that begins the moment HRIS posts a termination date. They watch for the event, map the user across every connected app, and fire SCIM calls that delete or suspend accounts without help-desk tickets. At the same time, the platform queries each service’s API to remove lingering OAuth grants, shut down service accounts, and claw back unused licenses so finance sees immediate savings.
- Time-boxed access automatically expires rights given to interns, vendors, or special projects after a predefined interval
- Zero-touch alumni lockouts bundle all deprovisioning steps into one preset playbook that never requires help-desk intervention
- Scheduled re-certification pings managers every quarter to confirm that remaining external accounts still make sense and remain safe
- Built-in audit trails export a minute-by-minute log that satisfies SOC 2 and ISO 27001 reviewers during assessments
Cutting mean time to deprovision from days to minutes shrinks the attack window and calms auditors who ask how “last day” equals “last login.” Teams also gain breathing room: no spreadsheet chases, no frantic password resets, and no surprise charges for seats no one uses. The process becomes muscle memory, not a fire drill, and the organization moves on knowing those back doors finally slammed shut.
Reining In Runaway SaaS Sprawl
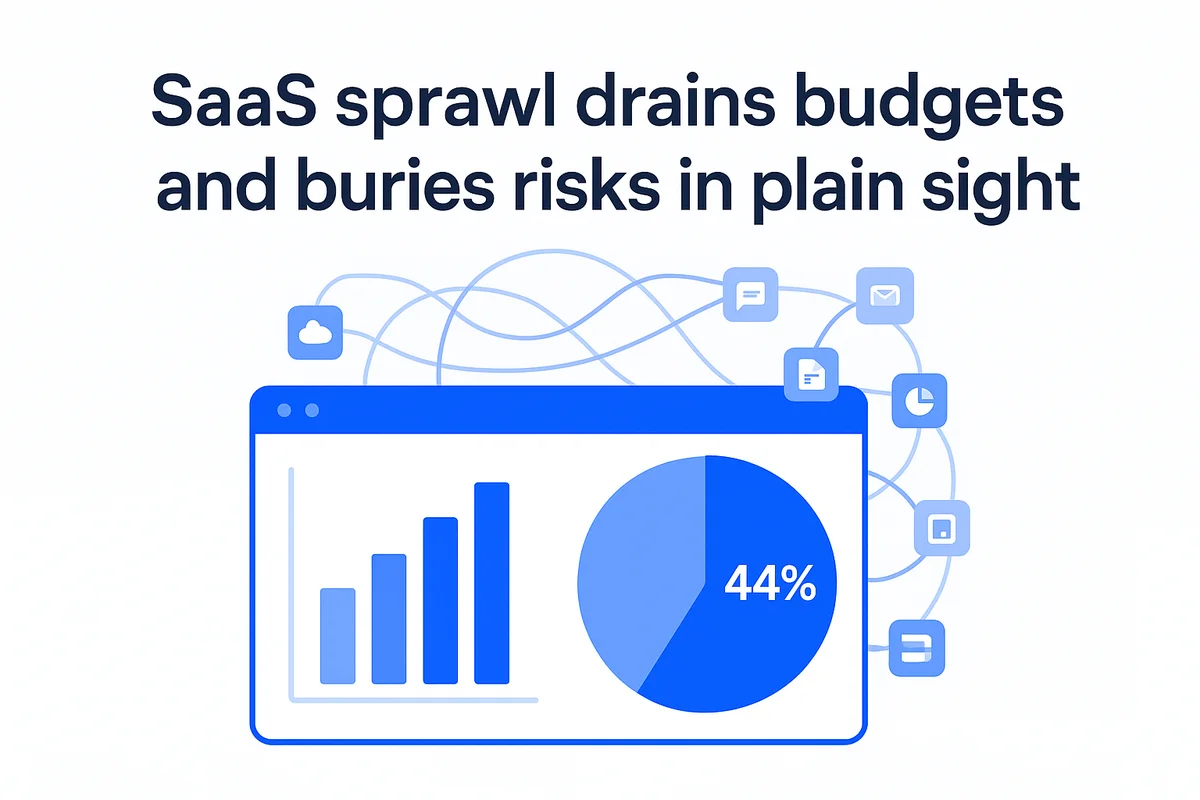
SaaS sprawl drains budgets and buries risks in plain sight. Finance signs one contract, marketing swipes a card for another. Before long, a single workflow hops across five tools, each holding its own slice of customer data. Security teams trace that path only to learn last quarter’s inventory is already obsolete.
Modern SaaS management tools surface every purchase the moment money or credentials move. They collect signals from expense feeds, SSO logs, browser extensions, and contract repositories. With data sources stitched together, IT leaders view real-time totals instead of year-old spreadsheets and finally know who owns what.
True governance demands more than tallying application icons on a screen. The same catalog powers license cleanup, patch coverage, and legal reviews without extra swivel-chair work. Zylo’s 2023 index shows 44 percent of paid seats sit idle; putting those numbers in one dashboard turns right-sizing into a weekly habit rather than an annual fire drill. Compliance teams review identical data to confirm each vendor’s data-processing agreement before a new region launches.
The platform turns insight into action by layering simple workflows over the catalog:
- Highlight overlapping tools with similar features and send a consolidation ticket to procurement
- Send critical patch alerts to the owner listed in the CMDB and escalate after 24 hours
- Auto-expire unused trials after 30 days to secure dormant data
- Export a living inventory to ServiceNow to seed architecture review sessions
The biggest payoff arrives when auditors request evidence covering every third-party system. A single export, stamped with timestamps and owner names, satisfies the ask in minutes and gives leadership a clear view of how quickly the stack keeps changing.
Standardizing Permissions for Least-Privilege Safety
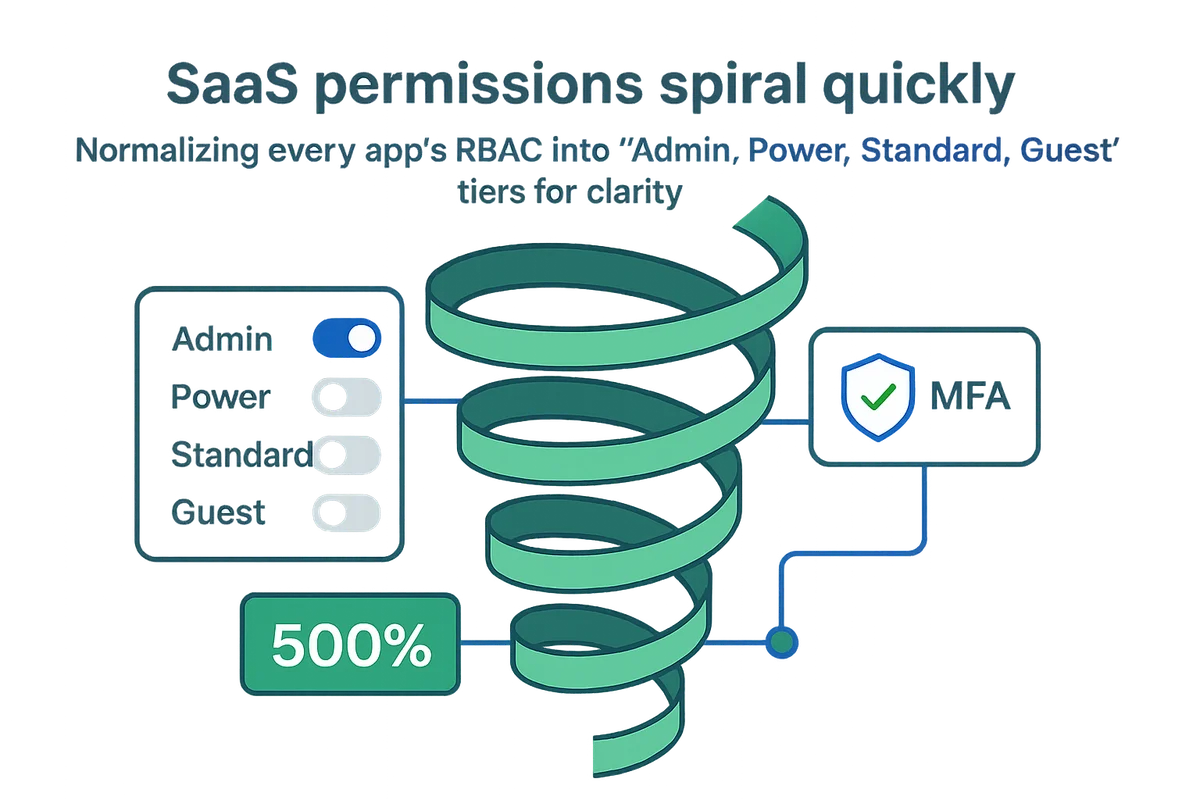
SaaS permissions spiral quickly when every application speaks a different security language. A marketing platform might surface fifteen role toggles, while a developer hub exposes raw OAuth scopes no one outside engineering deciphers. Teams grant “temporary” admin rights that outlive their need, and by quarter-end the audit log looks like alphabet soup. The mix results in privilege creep, spotty MFA enforcement, and a widening gap between policy and reality that attackers quietly leverage.
Many security teams now deploy SaaS management platforms to tame the chaos. The platform pulls role catalogs by API, maps them to a small set of company personas, and pushes corrections without waiting for an app release. Drift detection runs nonstop; if a user regains an admin badge after an update, the system can auto-downgrade the account or open a ticket in seconds. Key safeguards include:
- Normalizing every app’s RBAC into “Admin, Power, Standard, Guest” tiers for clarity
- Verifying MFA and SSO flags on each login endpoint, not just the primary domain
- Scanning OAuth grants for dangerous scopes like unrestricted read-write Git access
- Launching webhook-driven rollbacks when a setting violates baseline policy
Organizations that centralize SaaS controls often report rapid reductions in super-admin counts, faster remediation of risky OAuth scopes, and improved alignment with least-privilege policies across departments.
All events roll into one dashboard that exports plain-language evidence for ISO 27001, SOC 2, and cyber-insurance renewals. Internal audit no longer assembles screenshots; they filter by app, user, or date and pull a PDF in minutes. With fewer manual checks, analysts spend more time on threat hunting, and leadership finally treats least privilege as a measurable, sustainable practice rather than a feel-good slogan.
Conclusion
Security teams can’t keep overlooking shadow apps, orphan accounts, or the permission creep spreading across today’s SaaS stacks. The right management platform flags hidden tools, deletes ex-employee tokens, tracks every subscription, and compares roles with policy in one pass.
With that visibility, teams react faster, cut unused licenses, and hand auditors clear evidence that safeguards remain active. The same platform uncovers shadow IT, closes offboarding gaps, tames sprawl, and keeps access aligned to least privilege.
<div class="post-img">
<img src="https://ng-www.toriihq.com/articles/assets/images/articles/saas-management-cybersecurity_5.webp"
alt="A security team managing access controls and monitoring shadow IT in a modern SaaS environment."
class=" "
style="border-radius: 10px; max-width: 80%"
loading="lazy">
</div>
<figcaption></figcaption>
</figure>
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
You can learn more about Torii here.
Frequently Asked Questions
Shadow IT refers to unapproved software or services used within an organization, often leading to security and compliance risks due to lack of oversight.
SaaS management platforms enhance visibility by tracking unauthorized applications, enabling quick remediation, and ensuring compliance through active monitoring.
Orphaned credentials can lead to unauthorized access and data breaches, especially if former employees retain access to sensitive information after leaving.
Automated deprovisioning streamlines the process by instantly revoking access upon employee termination, reducing potential security vulnerabilities.
SaaS sprawl leads to budget waste, compliance challenges, and increased risks as multiple services manage sensitive data without centralized control.
Organizations can enforce least privilege access by standardizing permissions through a management platform, ensuring users only have necessary rights.
Integrated SaaS management solutions provide real-time insights into application usage, streamline compliance audits, and enhance security measures across the organization.